India unveiled its indigenous Aircraft carrier few days back raising hackles in the neighbourhood, not in Pakistan, but in China. Chinese media is claiming that now it will be easier for India to project its power in the Chinese area of interests like Strait of Malacca, South China Sea and the Pacific. However, these concerns are slightly exaggerated as this aircraft carrier may not be ready by 2020 and that India never moved its earlier aircraft carriers away from Indian region ever.
Nevertheless, one thing is for sure, if the upcoming sea trials would be successful, India can reduce its dependence on other countries for import of costly arms and weapons. It might make Russia, India’s top arm supplier, a bit uncomfortable, but looks like it is not so! Helping India achieve self-reliance was one of Russia’s calculated aim, which is why it ventured in many joint development and production of sophisticated weapons. Two friendly countries developing technology is always better than one country developing and other buying it.
 |
| INS Vikrant, credits on the image |
The new air craft carrier would give India further self-reliance in defence sector, which can reduce the import of costly arms and weapons. An aircraft carrier along with nuclear submarine is necessary for a navy to be called as a true blue navy. India is among the elite group of ten countries who possess an aircraft carrier in service at the moment. These countries are: US (10), Italy (2), UK (1), France (1), Russia (1), India (1), Spain (1), Brazil (1), China (1), and Thailand (1).
Last year China became third country in Asia to possess an operational aircraft carrier. It is a bit surprising that China, who loves to project its military power got its first aircraft carrier so late. China shared the same mentality of Soviet Union that a missile worth $1 million can sink a carrier worth $1 billion. Today when China’s economy is impressive, it doesn’t mind to roll out its own carrier in the blue waters.
In 1998, Ukrainian Trade Minister Roman Shpek announced that a Hong Kong based travel agency Chong Lot Travel Agency Ltd. has won the bidding of their retired aircraft carrier Varyag with $20 million. The idea was to convert the ship into a floating hotel and gambling parlour. However, China had bigger ambitions, it transferred the ship to a major Chinese Naval shipyard where it was renovated into an operational Aircraft Carrier. The ship initially lacked engines, a rudder and software.
In this article we will be comparing India’s first indigenous aircraft carrier and China’s first aircraft carrier Liaoning. Although the fair comparison would be between Liaoning and Vikramaditya as both belong to Soviet Era from their planning and that both will be operational after few months, we will be coming up with an article on that soon. Nevertheless, almost all of the development and construction of INS Vikrant was with India and most of the construction and development of Liaoning was with China. This makes it interesting to compare the technology and equipment incorporated by both.
Chinese Aircraft Carrier Liaoning (16)
Liaoning (16) became People Liberation Army’s Navy’s first commissioned aircraft carrier on September 25, 2012. Originally laid down as Riga on December 6, 1985 in Mykolaiv, USSR (present Ukraine), the ship was launched on December 4, 1988. In late 1990 it was renamed as Varyag. After the collapse of the Soviet Union, the ownership of the vessel was given to newly formed Ukraine. Since then the work on the ship had stopped. Varyag was structurally completed and had to be equipped with electronics. However, Ukraine considered holding the work and stripping the ship off important parts. In just seven years, in 1998 ship was put for auction without its engine, rudder and electronics.
In April 1998, Ukrainian trade minister confirmed the selling of Varyag aircraft carrier to China. After having huge political drama with Turkey for getting transit right from Black sea to Mediterranean sea through Turkish waters, the ship finally arrived in Chinese water after four years on February 20, 2002 taking a big round of Africa via Strait of Gibraltar, Cape of Good Hope and Strait of Malacca sailing with an average speed of mere 6 knots (11Km/h) completing a 28,200KM distance avoiding Suez Canal which doesn’t allow passage of dead ship and Indian waters which is full of diplomatic and political activities as India takes any Chinese action as alarming.
Varyag was docked in a dry dock in Dalian in June 2005. After six years on 10th August 2011, the ship began sea trials. The Ship was commissioned on 25th September 2012 as Liaoning. China claims it is a training ship and not operational however, sources declare that there are aircrafts in the hangar ready to fly and launch a mission.
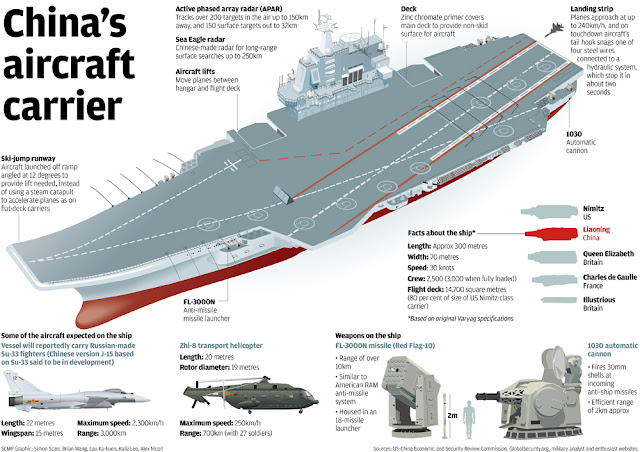 |
| Infograph – Chinese Aircraft Carrier Liaoning, credits on the image itself. |
Weapon Equipment
Liaoning is equipped with AESA and Sea Eagle (Type 381) 3D Radar developed in China. It has a range of 100 Km (62 mi) and Altitude of 8000m. The radar has the capability to track 10 targets simultaneously. Like almost all modern ships which have CIWS, Liaoning is equipped with three Chinese Type 1030 CIWS which has 10 barrels that can fire 30mm ammunition at the rate of 10,000 rounds/min. The Ship is equipped with Chinese FL-3000N SAM having maximum range of 9KM for subsonic targets and 6KM for supersonic targets. To protect itself from the submarines, it is equipped with ASW (Anti-Submarine Warfare) 12 tube rocket launchers.
INS Vikrant is equipped with Israeli ELTA MF Star Radar and Italian Selex RAN-40L radar. MF Star has the range greater than 25KM for low flying attacking missile and greater than 250KM for high flying aircrafts. Selex RAN-40L on the other hand has a maximum range of 400KM and minimum rang of 180m. In the area of early warning and enemy detection INS Vikrant has an upper hand. CIWS and LR SAM used in INS Vikrant is not known yet, once the information is available we will update soon. INS Vikrant is equipped with four Otobreda 76 mm Italian made compact cannon which has the capability to fire 120 rounds/min up to 20KM. Westland Sea King Helicopter will be primarily responsible for providing ASW capabilities to the Indian indigenous aircraft carrier. India has not declared yet if it has ASW rocket launchers on board INS Vikrant
Aircraft Carried
1) Liaoning can carry thirty Su-33 design based indigenous Shenyang J-15 Carrier based Multirole fighter aircrafts. The fighter is still in the testing phase and on 25th November 2012, two J-15 aircraft successfully made arrested landing on Liaoning.
2) Changhe Z-8 based on French Aérospatiale SA 321 Super Frelon helicopters will be used for Search and Rescue and Anti-Submarine Warfare operations. It is equipped with a surface search radar and a French HS-12 dipping sonar and carries a Whitehead A244S torpedo under the starboard side of the fuselage.
- Max. Speed: 249 km/h (135 kn (155 mph))
- Range: 1,020 km (549 nmi (632 mi))
- Rate of climb: 6.7 m/s (1,312 ft/min)
3) Ka 31 Helicopters will be used for airborne early warning
INS Vikrant on the other hand will carry twelve Mig 29K on board. The aircraft completed sea trials for the Indian Navy in November 2012.
Apart from Mig 29K, the ship will carry another eight naval version of India’s indigenous HAL LCA Tejas delta wing aircrafts. Which might take another many years to become operational.
Like China, INS Vikrant will also be carrying Ka 31 Helicopters for airborne early warning operations.
British Westland Sea King helicopters will be used for launching Anti-Submarine and Anti-Ship operations.
- Maximum speed: 129 mph (112 knots, 208 km/h) (max cruise at sea level)
- Range: 764 mi (664 nmi, 1,230 km)
- Rate of climb: 2,020 ft/min (10.3 m/s)
If the jets and helicopters of Chinese ship is compared with the Indian ones, India lacks considerably in this department. Chinese aircraft Carrier can carry 30 Aircrafts and 24 Helicopters Compared to 20 Aircrafts and 10 Helicopters by Indian carrier. It gives a good advantage to the Chinese over Indians especially when their primary jet J-15 outsmarts Indian Mig 29K.
However, at the moment, neither J-15 nor HAL Tejas is ready, Mig 29K is operational and will find place in Vikramaditya aircraft carrier as soon as it is delivered to Indian Navy.
Liaoning with its 2200 crew and 67500 tons displacement can sail with the speed of 30 Kn (55.56 Km/hr) whereas INS Vikrant with its 1,400 crew and 40,000 tons displacement can sail with the speed of 28 Kn (52 Km/hr)
The Chinese aircraft carrier appears to be a great giant with slightly more advanced fleet in front of INS Vikrant as well as INS Vikramaditya. J-15 is yet to prove its capabilities while Mig 29K still finds trust among Indians and Russians. 4++ generation MiG-29K is a combat hardened aircraft, which has the unique ability to even find and chase stealth aircrafts. It is only used by India and Russia and no other country. It is a carrier specific combat aircraft and Russian Naval Aviation has placed an order to get 24 more Mig29K/KUB between 2013 and 2015.
Unlike other ships, aircraft carrier requires much more skilled and experienced crew to take full advantage of its capability and when it comes to experience, India enjoys experience of operating many since 1961, which is more than 50 years. India even has a wartime experience during 1971 Indo Pakistan war when INS Vikrant (not to be confused with the latest one) helped Indian Navy form a naval blockade against Pakistan and bomb ports of Cox Bazar, Chittagong, Khulna and Port of Mongla as Pakistan Navy was trying to break through the Indian Naval blockade using camouflaged merchant ships. A PTI report of 4 December 1971 read, “Chittagong harbour ablaze as ships and aircraft of the Eastern Naval Fleet bombed and rocketed. Not a single vessel can be put to sea from Chittagong.”
China has declared that it will use Liaoning only for training purpose and as a model to develop new indigenous aircraft carriers. However, it sounds little tricky as China, which had not included any aircraft carrier before in its fleet because of cost issues, has now made a complete, full-fledged advanced ready to launch mission carrier. Another thing that strengthens the doubt is that Liaoning was supposed to be a floating casino and today it is allowing J-15 to make landings. It could be a training ship until J-15 becomes operational after that nobody knows what is China’s plan. Claiming it to be a training ship might be just a move to calm down the rest of the world, and save its image that it actually didn’t buy Varyag aircraft carrier from Ukraine to make its own functional and ready to launch mission carrier.
Both Indian and Chinese aircraft carrier are using the technology used in former Soviet aircraft carriers for take-off. They rely on Short Takeoff but Arrested Recovery (STOBAR) system for launching and recovering aircraft. Latest Aircraft carriers are using Catapult-Assisted Takeoff but Arrested Recovery (CATOBAR) system. STOBAR is easy to use, but limits the use of heavier aircraft and their payload. It is also difficult to operate bulky airborne early warning (AEW) aircraft using this system which can make the carrier very vulnerable during wartime. CATOBAR on the other hand is more advanced but needs precise designing and construction for it to function efficiently.
Indian Navy has taken the challenge to incorporate this latest technology in its second indigenous aircraft carrier, INS Vishal. For this, US based Northrop Grumman has offered to help India with the implementation of a steam catapult for CATOBAR on upcoming INS Vishal. Northrop Grumman expects if India develops and implements this technology on its aircraft carrier then it can become a good market for their E-2C Hawkeye AEW aircraft as CATOBAR system is ideal for launching bulky AEW aircrafts.
Now that both India and China have the capability to possess a true blue water navy. It would be interesting to see how both of them use their best assets to project their power and send warning. When Liaoning will be ready with J-15, it will be interesting to see whether China will send it first to deep Pacific or Indian Ocean.
Related Comparison Articles on The World Reporter
War and Military
How are Light Armored Vehicles Protected on the Battlefield?

When most people picture a military armored vehicle, they immediately think of the Main Battle Tank, a key player in battlefields around the world. But the Main Battle Tank is not the primary mobile platform for servicemen and women. Instead, that is the Light Armored Vehicle: a military vehicle that’s speedier and more agile than a tank, while offering far greater levels of armored protection, firepower, and maneuverability than a civilian vehicle such as a 4×4.
In order to be fit for purpose, Light Armored Vehicles must measure up to rigorous measures, including STANAG 4569, an assessment that shows their ability to deal with kinetic energy, artillery, and IED attacks. But how exactly do modern Light Armored Vehicles protect themselves on the battlefield? Here are five of the key attributes shared by today’s most popular vehicles.
It’s all about the armor
A Light Armored Vehicle’s name suggests that, well, it’s lightly armored. In fact, that’s something of a misnomer. A Light Armored Vehicle may not be quite the heavy-duty bruiser that a Main Battle Tank is, but don’t make the mistake of thinking that a vehicle such as this doesn’t boast some impressive protection in case it’s hit during an attack. While its armor plating is not as formidable as a Main Battle Tank, the standard model LAV-25 (the Light Armored Vehicle most widely used by the U.S. Army and Marines, alongside other armies around the world) still boasts light gauge high hardness welded steel armor that offers effective protection against small arms rounds, without adding unnecessary weight.
Its impressive suspension system also promises improved survivability against IEDs. Some of the current models of LAVs have been in service since the 1980s. But there have been upgrades, such as the LAV-25 A2, which offers increased external and internal ballistic armor upgrades, including protection from fearsome 14.5 mm armor-piercing rounds. When the LAV-25 models are superseded sometime this decade, armor-driven survivability will be one of the big areas that will get an overhaul. New breakthroughs in materials science are opening up fresh avenues for exploration in armor that is lighter weight, but tougher than existing forms of armor plating currently in use.
Blast-resistant seating
The increased use of improvised explosive devices (IEDs) as part of asymmetric warfare is a trend that has transformed battlefields over the past two decades. To protect the lives of crew travelling in Light Armored Vehicles, along with other combat vehicles, special blast-attenuating seats have been installed. Some manufacturers produce potentially lifesaving seating options to fit all crew positions, including commander, gunner, driver and troop seats.
Smart sensors
Protection can mean armoring. It can also mean ways to avoid risking taking hits in the first place. Fortunately, smart sensors have come on a long way in recent years — and make this second option more viable than ever. Modern Light Armored Vehicles increasingly boast sensors designed to sense, classify, track, and defeat incoming threats. One example is their impressively sensitive radar and jamming technologies. These can be used to counter threats like drones by severing the link between the drone and its controller, causing them to crash out of the sky. This may be vital in scenarios where an attack may involve weaponry a Light Armored Vehicle would not be able to adequately defend against with its existing armor. Sensing the threat ahead of time means being able to take proactive steps to counter and avoid it.
The best defense is a good offense
Smart sensors are one proactive way for Light Armored Vehicles to protect themselves. Another is using offensive weapons. The LAV-25 boasts a two-person powered turret fitted with a 25 mm M242 “Bushmaster” chain gun. Internally, it features firing ports which can allow six fully-equipped infantrymen to defend the vehicle using personal weapons. There is additionally a 7.62mm machine gun in co-axial mounting for carrying out anti-infantry defense. If required, a second 7.62mm machine gun can also be mounted along the turret roof. Variations of the LAV-25 can be — and have been — fitted with anti-tank guided missiles, superior unmanned turret, mortars, 5-barreled Gatling cannons, Stinger missiles, smoke grenade dischargers, and more. Though Light Armored Vehicles are not intended to replace a Main Battle Tank, these vehicles can more than hold their own in the field of combat when required. And, as many a good strategist has noted, the best defense is a good offense.
Tires
Compared to the tracks used by Main Battle Tanks, Light Armored Vehicles far more closely resemble civilian 4x4s. But the rigors of travelling in warzones is very different to the requirements of driving on even the toughest of terrains in the civilian world. One of the key points of protection for a Light Armored Vehicle is its ability to easily traverse difficult terrain. That comes in handy when you’re avoiding threats such as IEDs which make travelling along ordinary roads prohibitive. Features such as Central Tire Inflation Systems (CTIS) help these military vehicles with better all-wheel drive performance and mobility. Many have a “limp home” feature that can allow them to carry out limited travel even in the event of major tire leaks. That avoids the risk inherent with a Light Armored Vehicle being rendered totally disabled on the battlefield.
Technology
Concerns and Limitation of Cyber Warfare

The discovery of Stuxnet, a malware that targeted a nuclear facility, was somewhat revolutionary and groundbreaking. It targeted ICS which monitor and run industrial facilities. Before that, most of malicious programs were developed to steal information or break-in into financial sector to extort money. Stuxnet went beyond went and targeted high-level facilities. It is not hard to imagine what damage it could have inflicted if the worm were not detected. What is more worrisome, the technology is out. It might not be perfect, but it is definitely a start. Regardless of the intentions behind Stuxnet, a cyber bomb has exploded and everyone knows that cyber capabilities indeed can be developed and mastered.
Therefore, if they can be developed, they will probably be. The final goal of Stuxnet was to affect the physical equipment which was run by specific ICS. It was done in order to manipulate computer programs and make it act as an attacker intended it to act. Such a cyberattack had a particular motivation; sabotage of industrial equipment and destruction could have been one of the goals. So, if they were indeed the goals, it might have been an offensive act, conducted by an interested party, presumably, a state for its political objective. Yet, there are certain limitations when it comes to so-called “cyber weapons” (malware that might be employed for military use or intelligence gathering).
One of the main concerns of cyber offence is that code may spread uncontrollably to other systems. In terms of another physical weapon, it is like a ballistic missile that anytime can go off-course and inflict damage on unintended targets and/or kill civilians. Cyber offensive technology lacks precision, which is so valued in military. For example, in ICS and SCADA systems one may never know what can backfire because of the complexity of the system. The lack of precision consequently affects military decisions. When launching a weapon, officers should know its precise capabilities; otherwise, it is too risky and is not worth it.
In case of Stuxnet, the program started replicating itself and infected computers of many countries. For this moment we do not know if it were planned in that way. However, provided that that target was Natanz facility, it is unlikely. Symantec Corporation started analyzing the case only with external help; it did not come from Natanz. This exacerbates the case if a country decides to launch an offensive cyberattack.
If the military planning cannot prevent cyber technology to go awry or to go out in the public, it brings more disadvantages than advantages. Moreover, given a possibility of the code being discovered and broke down to pieces to understand what it does, it may potentially benefit an opposing party (and any other interested party along the way). This is unacceptable in military affairs.
Similarly, when the code is launched and it reaches the target, it can be discovered by an opponent. In comparison to nuclear, when a bomb explodes, it brings damage and destruction, but its technology remains in secret. In case of cyber, it may not be the case, as when a malware/virus is discovered, it can be reverse engineered to patch vulnerability. By studying the code, an enemy would find out the technology/tactics used that could be unfavourable in the long-run for the attacker.
Additionally, it should be said that not every malware is meant to spread by itself. In order to control the spread, vulnerability can be patched, meaning updating the software which had that vulnerability. An anti-malware can also be introduced; this will make the computer system immune to that particular vulnerability. Nonetheless, if the malware spreads uncontrollably, there is nothing much that an attacker can do. It is not possible to seize the attack. In this scenario, an attack may only release information about this certain vulnerability so that someone else can fix it. However, a state is highly unlikely to do so, especially if the damage is extensive. It would not only cost the state diplomatic consequences, but also it might severely impact its reputation.
An AI-enabled cyberattack could perhaps fulfill its potential. That means involvement of artificial intelligence. AI systems could make digital programs more precise, controlling the spread. In contrast, it could also lead to a greater collateral damage, if a system decides to target other facilities that may result in human death. Similar concerns are raised in the area of autonomous weapon systems in regard to the need of leaving decision-making to humans and not to technology. AI technology has a potential to make existing cyberattacks more effective and more efficient (Schaerf, 2018).
Aforementioned concern leads to another and affects the end result. When a certain weapon is employed, it is believed to achieve a certain goal, e.g. to destroy a building. With cyber capabilities, there is no such certainty. In the
Alternatively, the true costs of cyberattacks may be uncertain and hard to calculate. If that is so, an attacker faces high level of uncertainty, which may also prevent them from a malicious act (particularly, if nation states are involved). However, the costs and the benefits may always be miscalculated, and an attacker hoping for a better gain may lose much more in the end (e.g. consider Pearl Harbour).
Another concern refers to the code becoming available to the public. If it happens, it can be copied, re-used and/or improved. Similar concerns in regards to proliferation and further collateral damage emerged when Stuxnet code became available online. An attacker may launch a cyberattack, and if it is discovered, another hacker can reverse engineer the code and use it against another object. Moreover, the code can be copied, improved and specialized to meet the needs of another party. Technology is becoming more complex, and by discovering a malware developed by others, it also takes less time to produce a similar program and/or develop something stronger. (For instance, after Stuxnet, more advanced malwares were discovered – Duqu and Flame).
Furthermore, there are other difficulties with the employment of cyber offensive technology. In order to maximize its result, it should be supported by intelligence. In case of Stuxnet, an offender needed to pinpoint the location of the facility and the potential equipment involved. It has to find zero-days vulnerabilities that are extremely rare and hard to find[1]. Cyber vulnerability is all about data integrity. It should be reliable and accurate. Its security is essential in order to run an industrial infrastructure.
After pinpointing vulnerability, security specialists need to write a specific code, which is capable of bridging through an air-gapped system. In case of Stuxnet, all of abovementioned operations required a certain level of intelligence support and financial capability. These complex tasks involved into development were exactly the reason why Stuxnet was thought to be sponsored and/or initiated by a nation state. If intelligence is lacking, it may not bring a desirable effect. Moreover, if cyber offense is thought to be used in retaliation, malicious programs should be ready to use (as on “high-alert”) in the event of necessity.
Regardless of some
advantages of cyber offence (like low costs, anonymity etc), this technology
appears to be unlikely for a separate use by military. There is a high level of
uncertainty and this stops the army of using technology in offence. Truth is
when you have other highly precise weapons, it does not make sense to settle
for some unreliable technology that may or may not bring you a wanted result.
Yet, other types of
cyberattacks like DDoS attacks can give some clear advantages during military
operations and give an attacker some good cards in case of a conflict. When
such attacks used together with military ground operations, they are much more
likely to bring a desired result.
[1] For better understanding, out of twelve million pieces of malware that computer security companies find each year, less than a dozen uses a zero-day exploit.
War and Military
Swedish subs: a relic of the past?
As part of the program to replace its four Walrus-class submarines, the Dutch government is examining offers submitted by four European companies. It will announce by the end of the year which two competitors have been selected for the next negotiation stage.
Last June, Swedish Saab Kockums and Dutch partner Damen unveiled an initial design of submarine as part of their proposal to replace the Dutch Royal Navy’s fleet. During the European naval show in October, they further revealed technical details about their offer. Despite these announcements, Saab Kockums appears far from being able to draft more than drawings as it lacks the technology and manpower required to build submarines.
Kockums, a Swedish shipyard now known as Saab Kockums, made international headlines back in the 1990s when it closed a major deal with the Australian Navy to design their submarines fleet. Since then, the company seems to have become an empty shell.
In 2005, to strengthen its market position, Kockums joined its German competitor TKMS. Their partnership soon deteriorated as Kockums failed to attract new clients and retain old ones. The A26-class Kockums was developing did not sell well on the international market. Designed in the early 1990s, this sub class was considered outdated and too pricy. In 2013, after 20 years of cooperation, Kockums lost a contract with Singapore. Although TKMS eventually managed to win that contract thanks to another subsidiary, it led to increased tensions between the two companies.
In 2014, Russia’s realpolitik and the Ukrainian crisis led the Swedish government to reconsider its naval capabilities. The government realized the capacity to build submarines was of strategic importance, calling for Swedish companies to maintain an adequate level of competency. The Parliament decided to renew its subs fleet and promote local skills by ordering two updated ersatz of the A26-class to Kockums. However, the Swedish government failed to agree on the price with TKMS, ending the negotiation. At the height of the crisis, Swedish military authorities stormed Kockums’ laboratory in Sweden to retrieve technology that, according to them, belonged to the army. After that incident, deemed unusual by military experts, TKMS entered talks with Saab to sell Kockums. The sale was eventually closed later that year.
Over the past decades, U-boots have evolved from a fighting device to a diplomatic, sovereignty and intelligence tool. It is now used to locate enemies, deploy elite troops, collect data and send political messages. They require cutting-edge technology and constant research and development. Of all naval solutions, designing subs poses the greatest technical challenges and hence require special skillsets. Not keeping up with the fast-changing evolutions can quickly become the death knell of subs’ designers. Though Kockums prove to be a competitive submarine maker in the 1990s, not constructing subs over the last two decades means they have lost their technical and technological expertise. The price at which the company was sold is quite revealing. First thought to be worth 1 billion kronor, Kockums was sold for 340 million kronor (US$ 50,4 million).
The Dutch Navy is internationally recognized for the role its subs played in reducing piracy in the Gulf of Aden. It is part of the few countries able to furtively navigate oceans. The construction of its new submarine fleet is scheduled to start in 2021 and be operational by 2027. Saab Kockums is offering its updated A26-class and it might not be able to meet the deadlines. The A26-class has never been built before and, even if its design has been updated, the scope of the technical adjustments needed for this class to function smoothly is not yet known. With the technology used in naval solutions rapidly evolving, it might as well be less time-consuming to develop an entirely new class rather than update an ancient model.
Moreover, there are doubts about Saab Kockums’ capacity to continue its activities in a few years from now. The company already inked several deals with the Swedish Navy. However, to be able to keep up with the investments needed in research and development, Saab Kockums must succeed on export markets. If it fails to secure multiple deals abroad, it will eventually go bankrupt. With such scenario, betting on them might not be the smartest move.
The future does not look bright for Saab Kockums. Though signing with the Dutch Navy could temporarily be good news for them, without sustainable investments in research it will go down like a lead zeppelin!
-

 Business12 months ago
Business12 months agoHow To Future-Proof Your Business With The Right Tools
-

 Travel10 months ago
Travel10 months agoTravelling from San Antonio to Guadalajara
-

 Travel7 months ago
Travel7 months agoTravel wellness tips for a healthier and more enjoyable journey
-

 Europe5 months ago
Europe5 months agoRecent Books by Boaventura de Sousa Santos: Law, Colonialism, and the Future of Europe















